Google Workspace is considered by many to be the best productivity suite available.
It is particularly well suited to geographically dispersed staffing complements or companies with staff on the road. Google Workspace excels with its ability to facilitate collaboration. It not only facilitates sharing but also tracks changes across documents, sheets and projects.
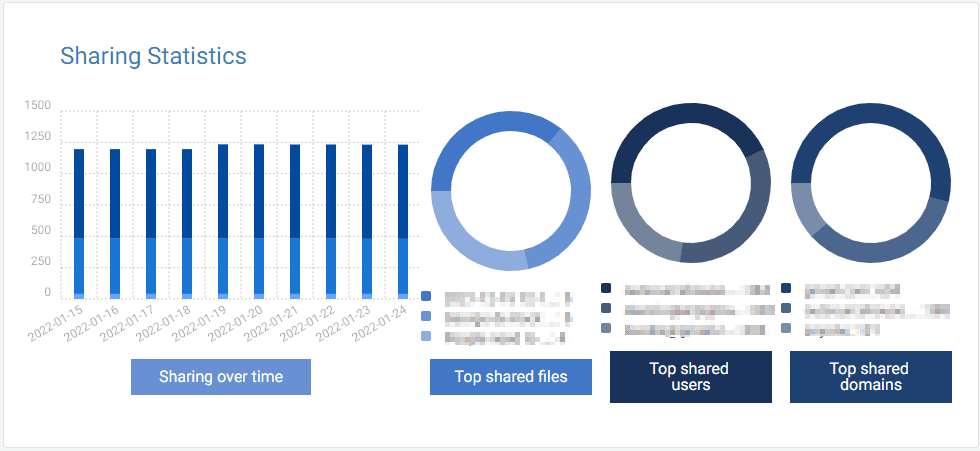
Sharing is a vital component of collaboration between staff, departments and clients. What is also crucial is being able to track and manage exactly what is shared and with whom. You need to know if the document, or sheet, should still be shared or if it’s confidential information that should never be exposed to outside, or even, limited internal parties.
The
Tricent Compliance Tool makes this essential management and tracking not only easy, seamless and centrally managed, but also co-opts staff into being part of the management and assessment of what should be shared and when. It allows for sharing privileges to be revoked, when appropriate, like when a staff member leaves or their role and responsibilities with the company change.
Network security, including cloud networks, is indispensable to the health of any company to protect IP and other proprietary information. With the promulgation and proliferation of privacy legislation, entrepreneurs and business entities are required to protect other stakeholders as well.
Laws, such as, the California Consumer Privacy Act (
CCPA) in America, the General Data Protection Regulation (
GDPR) in the European Union and the Protection of Personal Information Act (
POPI Act) in South Africa and others around the world, mean that failing to secure data has further implications for companies. We are no longer only concerned with protecting our data, but are required to secure the information we hold about clients, suppliers and other business partners.
Tricent Compliance Tool makes it simple, automated and streamlined to ensure compliance, not only with the requirements of external parties, but also with your internal security policies.
It also means that this important task doesn’t fall off the to do list. When the binary code hits the fan, it’s too late to point fingers or figure out who didn’t get to this task on their to do list. This tool gives you peace of mind that this must do task is handled.
As business owners and managers, it can sometimes be difficult to share, because we understand the risk and implications of details ending up in the wrong hands.
Like an insurance policy, this compliance tool engenders trust between owners, managers, IT security teams and staff because it’s continually performing a security audit of what information is being shared and who has access to it. It runs in the background and prompts you to assess if sharing rights fall within the company policies or need to be adjusted.
Staff being emailed regularly by a tool that tracks what they are sharing, or attaching to emails, could have the added benefit of being a proactive step that shuts down any possibility of nefarious activity.
If you want more control, you can lock the sharing abilities of your staff or decide, at a moment’s notice, to remove all the shared files and folders right now.
This compliance tool moves you from being in the dark about your company’s exposure and risk to placing the reins of control in your hands, where they should be.
As the saying goes, don’t shut the barn door after the horse has bolted.
Contact us for a view into your exposure, a product demo, pricing and expert advice on how best to set up your control policies. We are global resellers for the Tricent Compliance Tool and can provide pricing in USD.